Introducing Evervault Page Protection: Securing payment pages from JavaScript attacks
Secure your payment pages against script and security header attacks while complying with PCI DSS 4.0 requirements, 6.4.3, and 11.6.1.


Given it is the end of the year, we thought we’d reflect on all the products and features we’ve shipped this year. However, doing a ‘quick roundup’ of this year’s releases is... lengthy, to say the least, so we decided to highlight some of our favorites. In order of appearance…
We kicked off the year with a fresh coat of paint on Evervault.com
In February, we added two key features to Inputs, making collecting user cards much more flexible:
disableCVV boolean can now be passed to Inputs. When set to true it will prevent Inputs from rendering that field. The Supported Settings section of the Inputs docs has been updated to reflect these changes.As part of a broader effort to improve the tail latency of requests to E3, the default elliptic curve used throughout the system was migrated in March from SECP256K1 (best known as the Bitcoin curve) to SECP256R1. This migration increased the throughput of individual encrypt operations by 4x.
In March, we also made the source code for our Cages product publicly available. This allows developers to view the code deployed alongside their process in an enclave. This is crucial for one of Cages' main features: cryptographic attestation. Developers can now verify that the official Cages runtime and their own process are running untampered within the enclave. You can access the source code for the Cages runtime and the associated CLI on GitHub. Check out our deep dive series on how we built Cages, starting with Building Enclaves Easily.
Developers can verify that the official Cage runtime and their own process are running untampered within the enclave. Throughout the year we released a series of features which made it easier for developers to leverage the security offered from attestation. Some highlights include:
March also marked the launch of Evervault Guides, a new section of our documentation dedicated to providing instructions on building common use cases with Evervault across various tech stacks. Each guide includes a link to a Replit with runnable code and a GitHub repository that can be configured for easy following. Some notable highlights include:
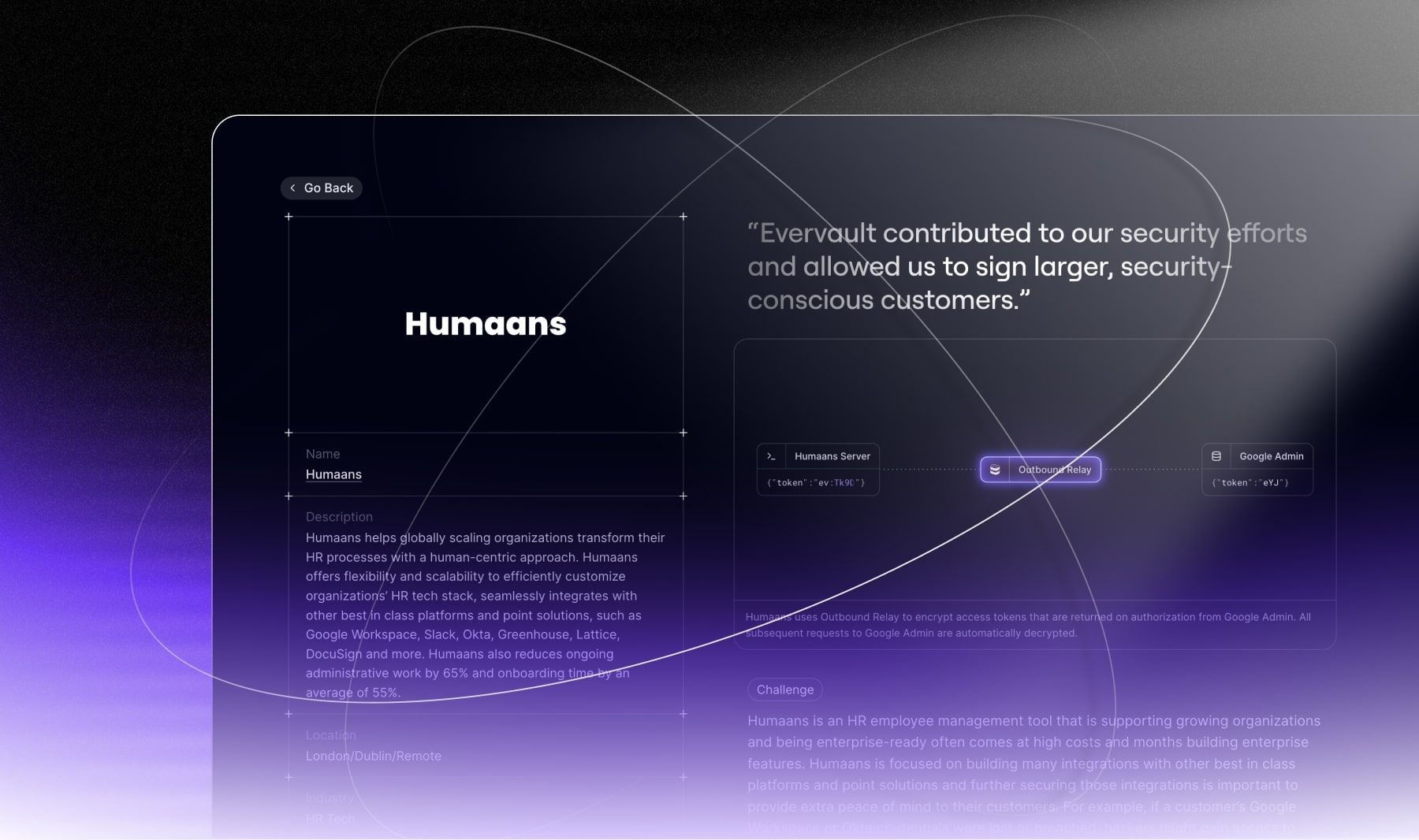
In April, we created a page to highlight the innovative ways our customers are utilizing Evervault. Check out how Humaans encrypts third-party API credentials or how Meili achieved PCI compliance in days.
If you're interested in seeing it in action, take a look at how Swan encrypts customer video files.
Launching the Decrypt API gave Evervault customers the ability to perform one-time decryption of their previously encrypted data, allowing them to create entirely new workflows. The API has been integrated into all of our SDKs, making it effortless to begin. Furthermore, the Decrypt API is accessible as a standard REST API for platforms that currently lack SDK support. In addition to the flexibility provided by the Decrypt API, we have also introduced an Encrypt API that simplifies programmatic data encryption. Check out the docs to get started with the Decrypt API.
In July, our founder Shane started a podcast! Join the team as we "decrypt" data security and development across the industry. Each episode features guests from Vanta, Tines, Circle, and other security leaders. They discuss how teams handle sensitive customer data, address technical challenges, and navigate the ever-evolving industry trends.

In August, we revamped our PCI Compliance solution to include our latest product features and extended compliance service. Using Evervault to accelerate PCI compliance allows you to collect and process cardholder data without the usual regulatory and compliance challenges. We follow a few simple steps to expedite time-to-compliance:
To learn more about our PCI Compliance solution, or to schedule a consultation with our team, simply respond to this email.
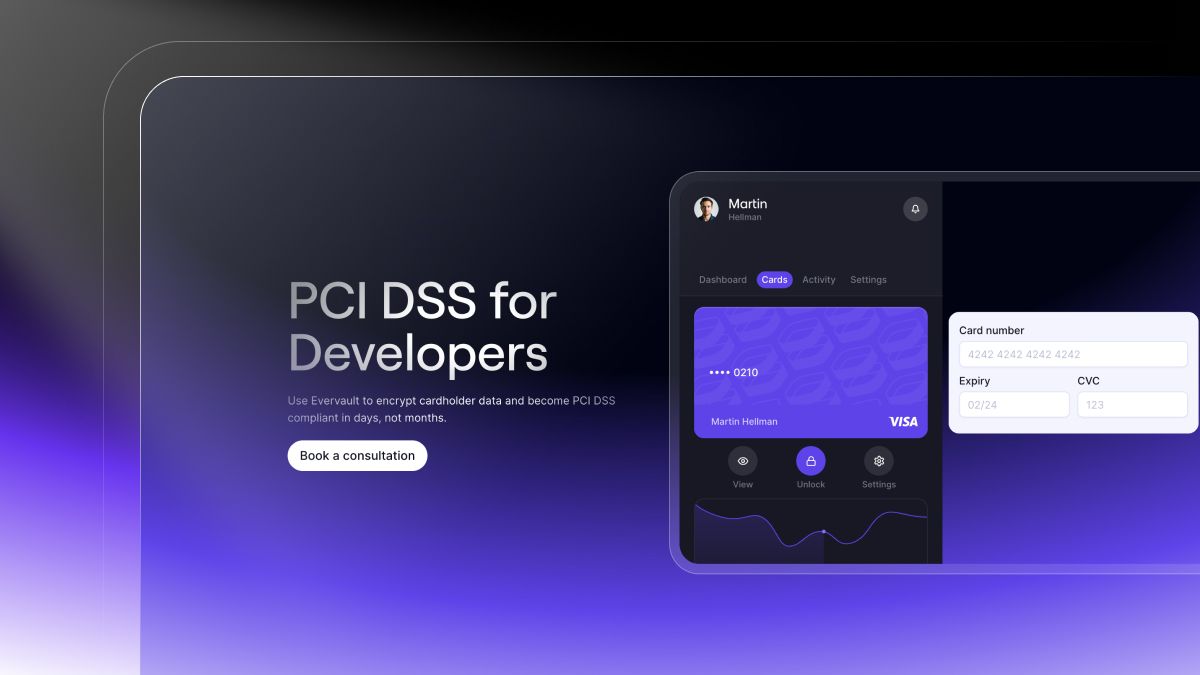
Reveal allows you to display plaintext cardholder data to your end users without increasing your PCI Compliance scope. Encrypted cardholder data from Evervault can be securely passed to Reveal, which is a hosted secure iframe element. This workflow ensures that the plaintext cardholder data never touches your infrastructure, thereby minimizing your PCI compliance scope.
Reveal is fully customizable and can be easily updated to match your design system using a simple CSS configuration.
To get started, please refer to the Evervault Reveal docs at https://docs.evervault.com/products/inputs#reveal.
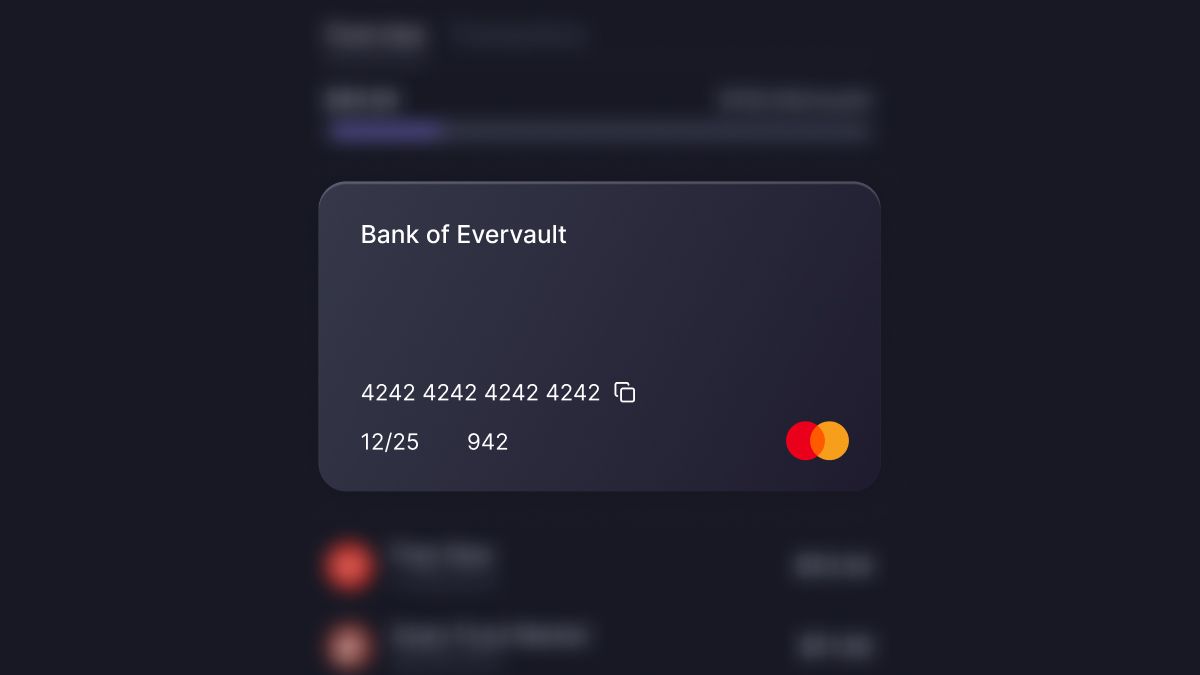
A couple months ago, we introduced Client Side Tokens. These are versatile and short-lived tokens that frontend applications can utilize to perform various actions, like running Functions or decrypting data. Client Side Tokens are restricted to specific payloads.
By default, a Client Side Token will live for 5 minutes into the future. The maximum time to live of the token is 10 minutes into the future. When using the REST API, the expiry field must be in epoch milliseconds. Take a look at our docs if you’re interested.
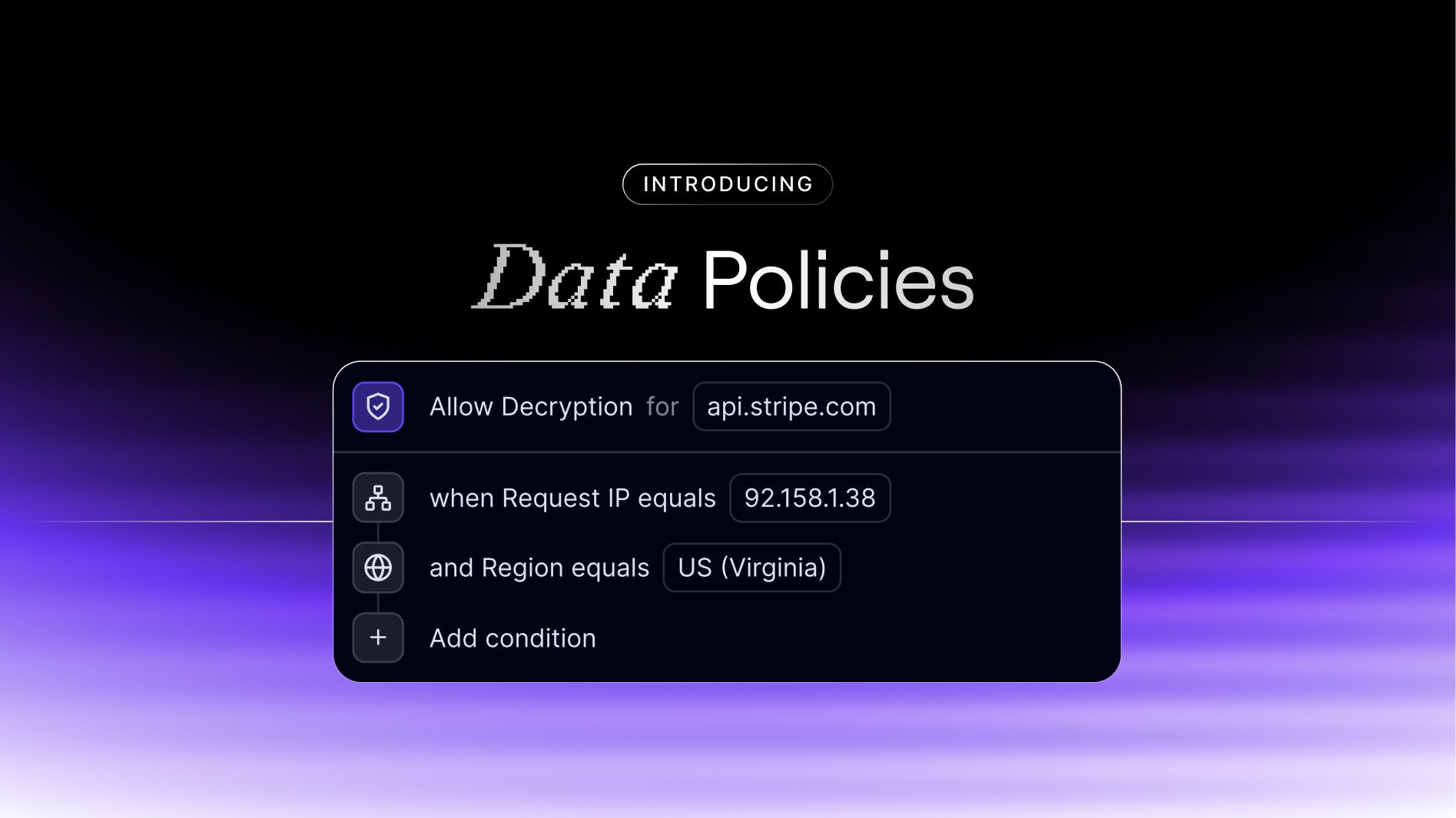
In November, we launched Data Policies, the newest feature in Evervault's core platform. Data Policies guarantee that when you encrypt sensitive data, that data can only be used for its intended purpose.
Data Policies are a set of conditions that you establish, which determine how and when data can be decrypted. These can be based on a multitude of parameters such as the type of data, its geographical location, a timestamp, or specific user permissions.
By incorporating this added functionality into Evervault's encrypted data workflows, the risk of data misuse is reduced, resulting in significantly hardened data security.
Read about the full release here
If you want to take a closer look, check out any of this year’s updates:
Lastly, thank you for all your customer feedback and requests driving our roadmap; we love hearing from you on how you’re using Evervault in your product. We look forward to building with your projects in mind next year.